A Virtual Private Cloud (VPC) is an isolated virtual network environment within a public cloud provider's infrastructure that gives you complete control over your network configuration. Think of it as your own private section of the cloud where you can launch resources in a logically separated environment that you define.
Network Isolation: VPCs create a boundary around your cloud resources, separating them from other customers' resources and the public internet. This isolation is achieved through software-defined networking that mimics having your own physical data center.
IP Address Management: Each VPC comes with its own private IP address space that you define using CIDR blocks (e.g., 10.0.0.0/16). You have complete control over IP addressing, subnetting, and network topology within this space.
Virtual Networking Controls: VPCs provide networking features including subnets, route tables, internet gateways, NAT gateways, and security groups that control traffic flow and access to your resources.
Amazon Web Services (AWS VPC):AWS VPC allows you to provision a logically isolated section of Amazon's cloud where you can launch resources in a virtual network you define. You control network configuration including IP address ranges, creation of subnets, and configuration of route tables and network gateways.
Microsoft Azure Virtual Network (VNet):Azure VNet provides similar functionality to AWS VPC, enabling you to create isolated network environments within Azure. VNets support hybrid connectivity scenarios through VPN gateways and ExpressRoute connections.
Google Cloud Platform (VPC Network):Google Cloud VPC networks are global resources that provide connectivity for your cloud resources. Unlike AWS and Azure, Google's VPC networks are not bound to specific regions and can span multiple geographic locations.
Multi-Tier Application Architecture: Deploy web servers in public subnets with internet access while keeping database servers in private subnets without direct internet connectivity.
Hybrid Cloud Connectivity: Connect your on-premises infrastructure to cloud resources through VPN connections or dedicated network links, extending your data center into the cloud.
Development Environment Isolation: Create separate VPCs for development, staging, and production environments to ensure complete isolation and different security policies.
Compliance and Security Requirements: Meet regulatory requirements by implementing network-level isolation and controlling data flow between different application components.
Subnets and Availability Zones: VPCs are divided into subnets that can be public (with internet gateway access) or private (without direct internet access). Subnets are typically mapped to specific availability zones for high availability.
Route Tables: Control where network traffic is directed within your VPC and to external networks. Each subnet is associated with a route table that determines traffic flow.
Security Groups and NACLs: Provide stateful (security groups) and stateless (Network Access Control Lists) firewall capabilities to control inbound and outbound traffic at the instance and subnet levels.
Internet and NAT Gateways: Enable controlled internet access for resources within your VPC. Internet gateways provide direct internet access to public subnets, while NAT gateways allow private subnet resources to access the internet without being directly reachable from it.
VPC Peering: Direct network connection between two VPCs, allowing resources in different VPCs to communicate as if they were on the same network. Limited to same cloud provider and often same region.
Transit Gateway/Hub: Centralized connectivity hub that connects multiple VPCs and on-premises networks through a single gateway, simplifying network architecture.
Site-to-Site VPN: Encrypted connection between your VPC and on-premises network over the public internet, extending your network into the cloud.
Direct Connect/ExpressRoute: Dedicated network connection between your premises and cloud provider, bypassing the public internet for more consistent performance and enhanced security.
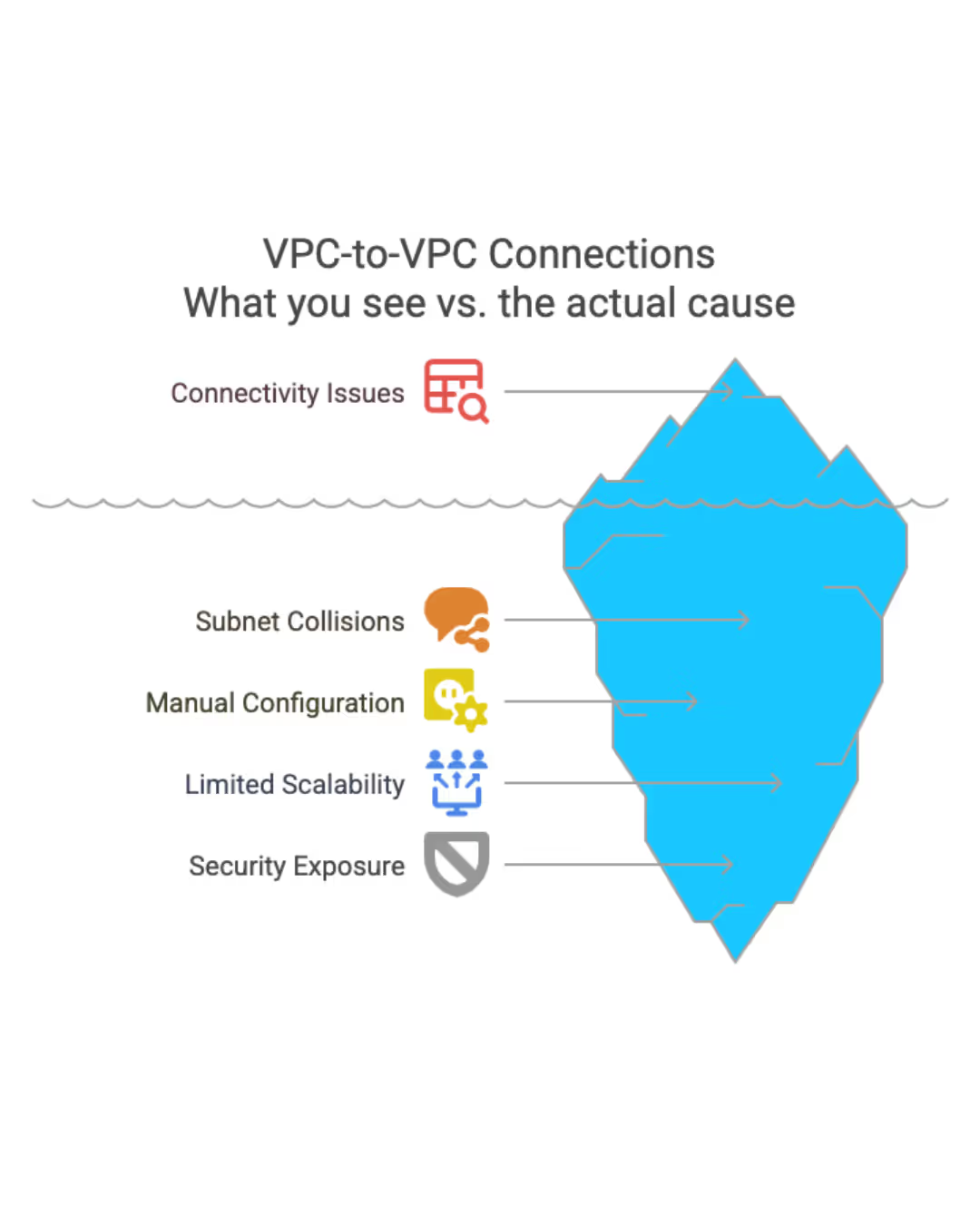
Cross-Cloud Complexity: VPCs are cloud provider-specific, making multi-cloud networking complex and requiring separate configurations for each platform.
IP Address Conflicts: When connecting multiple VPCs or hybrid environments, overlapping IP address ranges create routing conflicts that require complex NAT configurations or network redesign.
Routing Table Management: As networks grow, route table management becomes complex, especially when connecting multiple VPCs and on-premises networks.
Limited Cross-Region Connectivity: VPC peering and networking features often have regional limitations, requiring additional complexity for global applications.
Manual Configuration Overhead: Setting up secure, scalable VPC networking requires deep networking expertise and significant manual configuration.
Traditional VPC networking was designed for single-cloud, single-region deployments but modern applications require:
Understanding these VPC fundamentals helps explain why organizations increasingly need networking solutions that can operate above the cloud provider layer, providing consistent connectivity and security policies across any infrastructure.
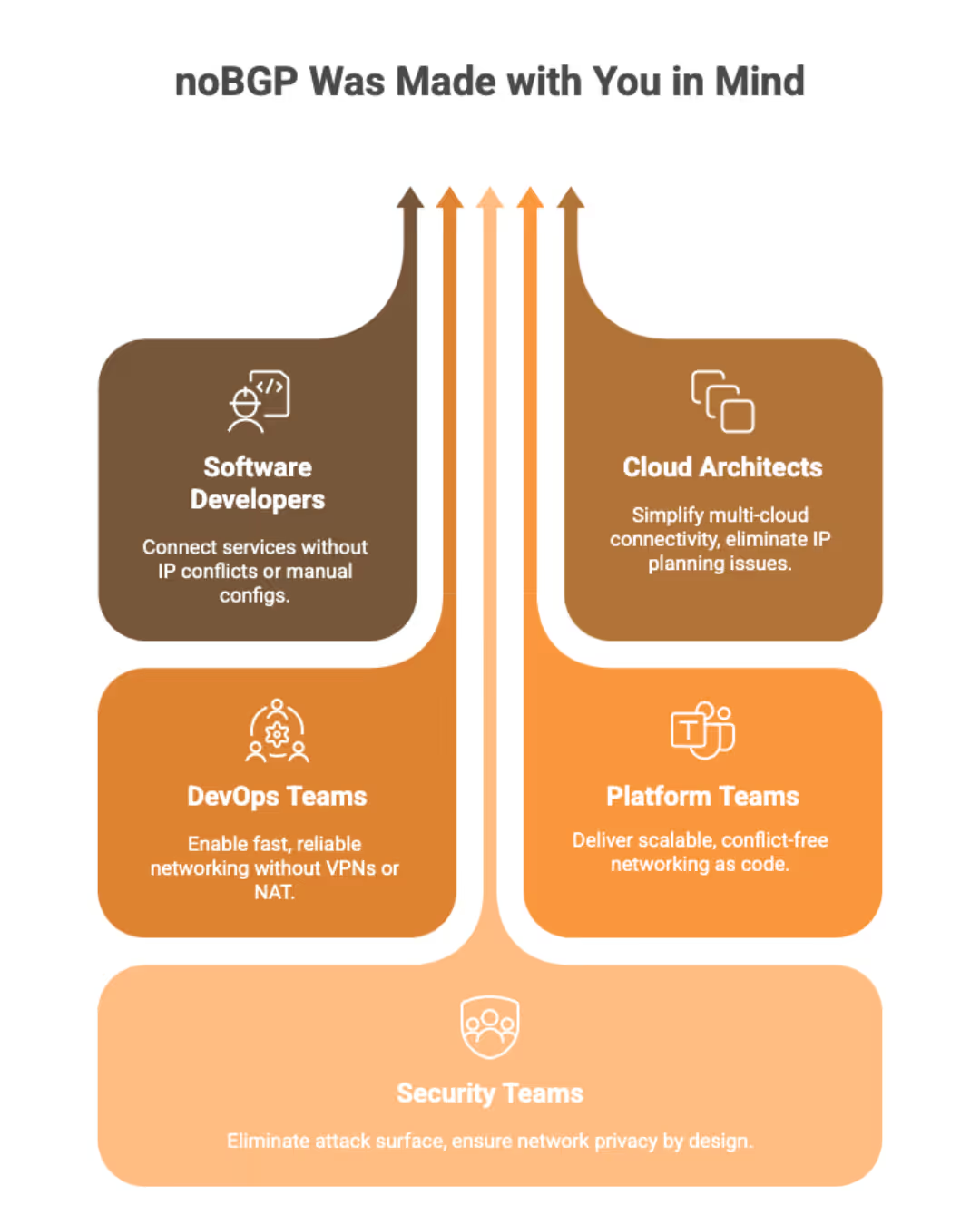
noBGP works with all cloud and data center providers including AWS, Azure, GCP, Oracle, Cachengo, Equinix, and more. There is no technology lock-in to specific vendors. Migrate your workloads to any location including on-premise environments.
Yes, noBGP creates private, encrypted connections without the complexity of VPN tunnels.
No. You can keep your existing CIDR blocks - even overlapping ones.
VPC Peering requires CIDR coordination and doesn't scale well. noBGP works even with overlapping IP ranges and simplifies operations. noBGP also works across accounts within a cloud provider or across multiple cloud providers.