The Problem with BGP: A Legacy Backbone in a Cloud-Native World
Border Gateway Protocol (BGP) is the foundation of today's internet routing, but it wasn't designed for what we ask of it today. BGP is:
- Non-deterministic. You don't control the exact path your data takes.
- Public and exposed. Traffic often travels across untrusted networks.
- Inflexible. Routing decisions depend on pre-established relationships and AS path preferences, not real-time policy.
- Opaque. There's little visibility or control once your data hits the wire.
Modern cloud-native architectures need routing that reflects business intent, compliance, performance, and security. BGP doesn't offer that.
Enter noBGP: Private, Deterministic Routing for a Multi-Cloud World
noBGP replaces BGP-based routing with a private, encrypted, policy-controlled network that spans clouds, data centers, and devices without the need for VPNs, NATs, or public IPs.
It's a private routing fabric where you choose the path.
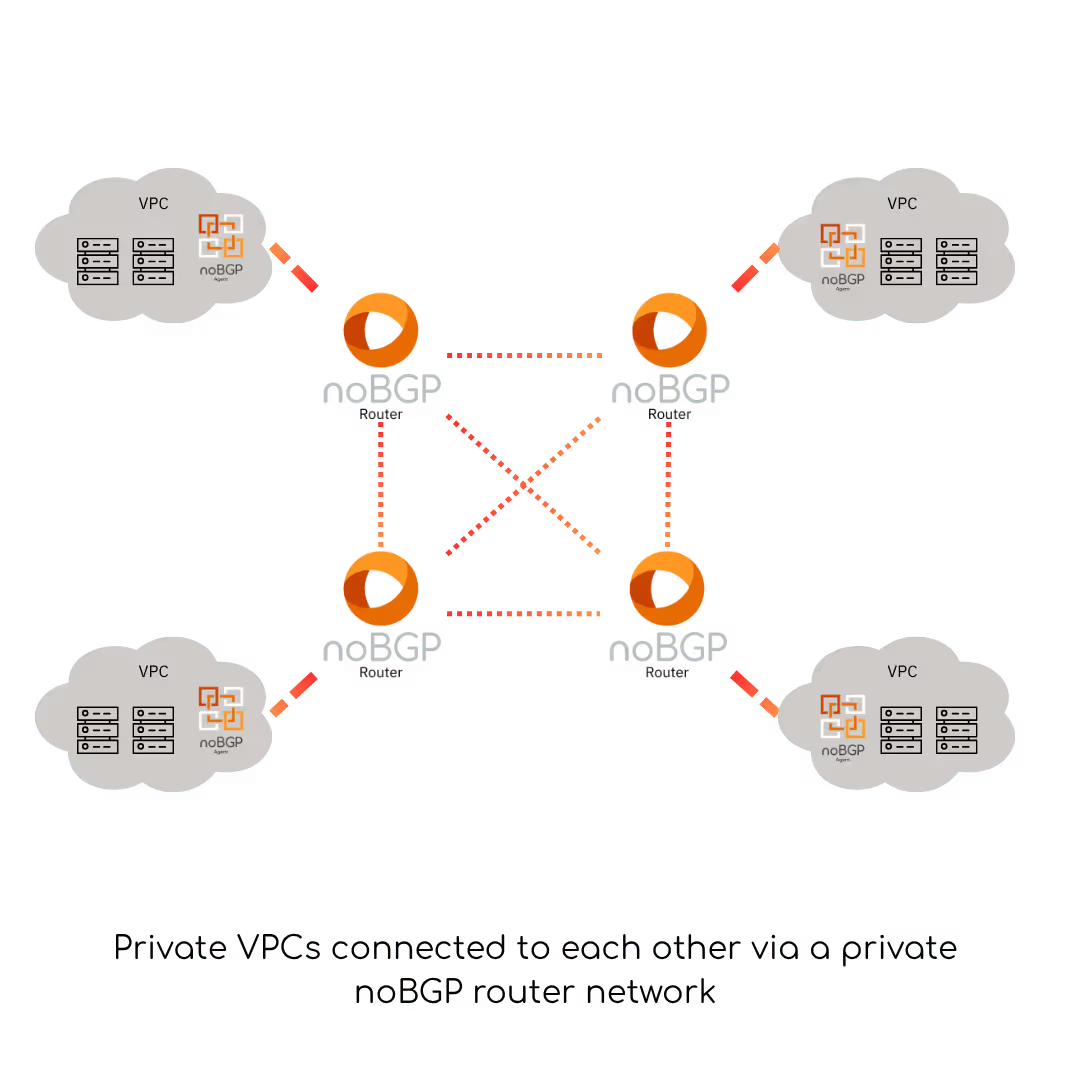
Architecture Overview
1. Agents
Lightweight software installed on or within VPCs, physical servers, or edge devices. Agents:
- Authenticate into one or more private networks
- Negotiate end-to-end encrypted sessions with other agents
- Disover and connect to the closest available router (via local discovery or central coordination)
- Allow authorized data to pass through the Agent to access private networks
2. Routers
Routers handle policy-driven transit across the noBGP fabric. Customers can:
- Deploy their own routers (e.g., one per rack in a data center, one per AWS Availability Zone or Region, etc.)
- Use noBGP's SaaS router network
- Mix both private and noBGP SaaS routers with control over fallback and path logic.
Each router receives traffic from a local agent, evaluates routing policy, and forwards traffic across the router network toward the destination agent, applying rules like:
- Latency or bandwidth optimization
- Trusted infrastructure only (e.g., utilizing your own or a partner's dark fibe)
- Geolocatin constraints (e.g., EU-onl paths, keep data off specific telco or cloud networks)
- Compliance zones (e.g., HIPAA, GDPR)
3. Private Networks
Agents belong to one or more private networks, which are:
- Fully isolated by design. No implicit trust or overlap
- Created and managed via the noBGP Admin UI or CLI
- Enforced with routing policy defined at the network level
Routing Behavior
Path Selection Logic
Admins define routing policies. They can specify whether to:
- Use customer hosted routers
- Use noBGP's SaaS routers
- Use any available router in the customer's trust domain
Policies also allow "NONE" selection which defers to BGP-style best-effort routing inside the noBGP fabric, used in less strict scenarios.
Dynamic Paths and Rerouting
noBGP is resilient and adaptive:
- Routers dynamically reroute traffic based on real-time link health
- Sessions remain intact even if IPs change (unlike traditional routing)
- Agents automatically re-establish local router connections as needed
End-to-End Encryption
All traffic is encrypted from agent to agent:
- A secure session key is negotiated directly between agents
- Routers cannot inspect or decrypt the payload
- This ensures data confidentiality across all hops, even across shared SaaS routers
Centralized Control, Local Enforcement
noBGP uses a centralized control plan to:
- Authenticate devices and networks
- Distribute router and agent configurations
- Push policy updates to all participating infrastructure
But the data plane is distributed. Routing decisions happen at the router level, and path selection is evaluated at each hop in real time, enabling both fine-grained control and low-latency response.
Why noBGP is Superior to Legacy BGP

Use Case Examples
Multi-Cloud service mesh without VPNs
Deploy agents into GCP, AWS, and Azure; define policies like "send all EU traffic through routers in Frankfurt only."
AI/ML workloads with bandwidth awareness
Train models on hybrid infrastructure while routing data through high-bandwidth paths, not cheapest or shortest ones.
Edge device connectivity
Deploy to thousands of IoT gateways. Agents find the nearest router, and all data is routed through verified, compliant nodes.
Conclusion
noBGP delivers what BGP cannot: secure, observable, deterministic paths across any infrastructure. Whether you're building resilient SaaS, hybrid cloud apps, or multi-region compute pipelines, noBGP gives you control over the invisible highways of your data.
You don't just hope for the best parth | Choose Your Path.

