Eliminate public exposure. Control every data path.
noBGP replaces BGP, VPNs, and firewalls with a modern security-first networking architecture invisible to attackers and visible only to you.
Modern cloud-native architectures need routing that reflects business intent, compliance, performance, and security. BGP doesn't offer that.
The internet was never meant to be secure
Engineers built legacy networks on the assumption of trust between devices, users, and networks. But this assumption no longer holds.
- Public IPs are a libability: Every exposed address invites scanning, probing, and attack.
- BGP routes are unpredictable: Your traffic crosses hostile or non-compliant regions without your knowledge.
- VPNs don't scale security: They create a single encrypted tunnel but not real segmentation or control.
- Misconfiguration is the #1 risk: Firewalls and ACLs are fragile, manual, and impossible to scale securely.
Every time you expose a service to the internet, you create an opportunity for attack. With noBGP, you don't need to expose anything.
Zero trust by design. Private by default.
Most networking tools add security after the fact. noBGP is different: starts with invisibility.
Eliminated attack surface
- No public IPs
- No open ports
- No inbound connections
- No DNS exposure
Deterministic Data Paths
- Policy-driven routing
- No dependency on BGP
- Full control over where your data travels
- Compliant by default
noBGP creates secure overlays only your workloads see and only the workloads your authorize to connect.
How noBGP secures your network
Unlike traditional networks routing traffic using public infrastructure and shared protocols, noBGP creates ephemeral, encrypted connections between your workloads. You define them using policy, identity, and region.
Agent-to-agent encryption
Agents initiate outbound connections. We never allow inbound access.
Service-level identity routing
We authorize each connection using workload identity and policy, not IP or port.
Policy-defined path
You control the routing. You define using geography, compliance zone, latency requirements, cost-optimization, or anything else.
Security benefits at a glance
- External IPs: Eliminated. Not Required.
- Inbound ports: Never needed. All traffic is outbound initiated.
- End-to-end encryption: We enforce at the session level, identity-based.
- Cloud-to-cloud security: Native, with no VPN setup required.
- East-West security: secure within data centers and clusters.
- Zero trust enforcement: Default. Identity and policy drive access.
- Compliance support: Enforce geographic routing and data locality.
- Attack surface: Invisible to unauthorized networks.
Secure by architecture, Not configuration
Security shouldn't depend on thousands of lines of ACLs, perfectly tuned firewall rules, or constant patching of exposed services.
With noBGP:
- There's nothing to scan
- Nothing to attack
- Nothing to misconfigure
Instead of bolting on security, noBGP removes the assumptions behind traditional network vulnerabilities.
You get:
- Default deny networking
- Encrypted service-to-service connections
- Policy driven path control
- We build zero trust in, not add later
Who benefits from noBGP?
- CISO: Minimize attack surface, simplify compliance, and reduce vendor risk
- DevOps: Build secure networks without mapping firewall rules or VPNs
- Compliance: Enforce data sovereignty and region specific routing policies
- Cloud architects: Connect across clouds and on-prem without public IPs or BGP tunnels
noBGP integrates seamlessly into DevOps pipelines, compliance workflows, and multi-cloud architectures. Whether you manage kubernetes clusters, legacy VMs, or hybdrid workloads: your network becomes secure by default.
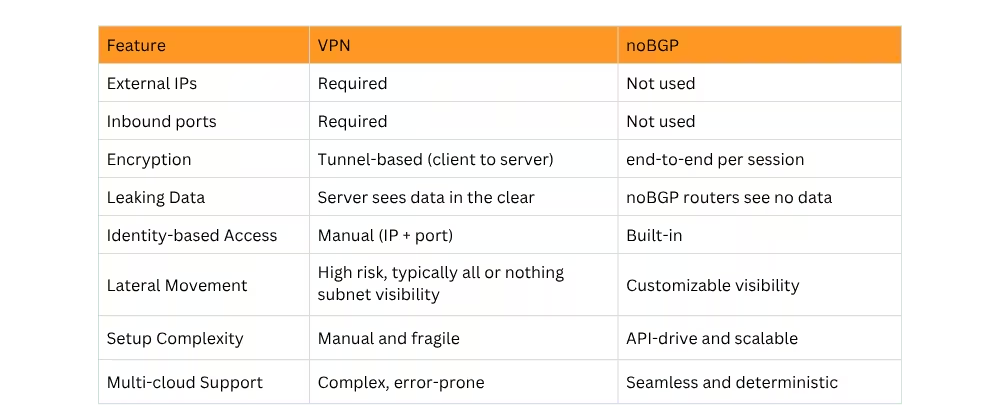
Legacy VPNs vs. noBGP
With VPNs, attackers target your tunnel endpoints. With noBGP, no endpoints exist for attackers to target.
See what secure networking feels like
Ready to experience a network with zero external exposure and total data path control?
- Free to start
- Works across clouds and on-prem
- API and CLI ready
