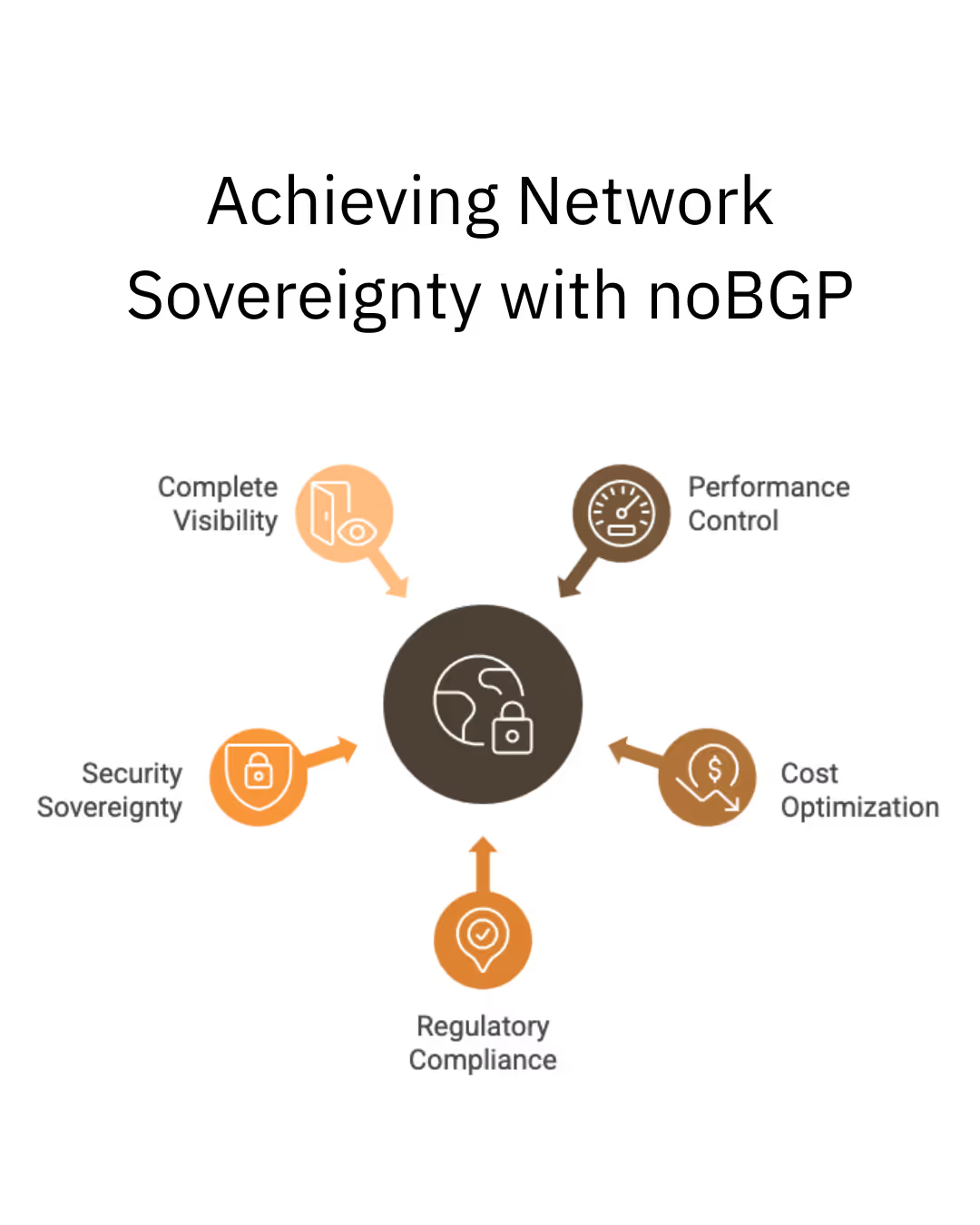
Network sovereignty is the ability of an organization to maintain complete control and authority over how its data travels across networks, independent of external routing decisions made by internet service providers, cloud vendors, or other third-party network operators. It represents the fundamental principle that you, not external protocols or providers, should determine the path, security, and policies governing your network traffic.
Regulatory Compliance Requirements: Modern regulations like GDPR, CCPA, and industry-specific frameworks increasingly require organization to demonstrate control over data flows. Network sovereignty provides the visibility and control necessary to prove compliance with data residency, transfer restrictions, and access controls.
Geopolitical Risk Management: As international tensions affect internet infrastructure, organizations need to avoid routing data through adversarial countries or regions where it could be intercepted, modified, or blocked. Network sovereignty enables explicit geographic routing controls.
Security and Zero-Trust Architecture: Traditional networking assumes network location indicates trust level. Network sovereignty implements identity-based security where connections are authorized based on cryptographic credentials rather than network addresses, supporting true zero-trust principles.
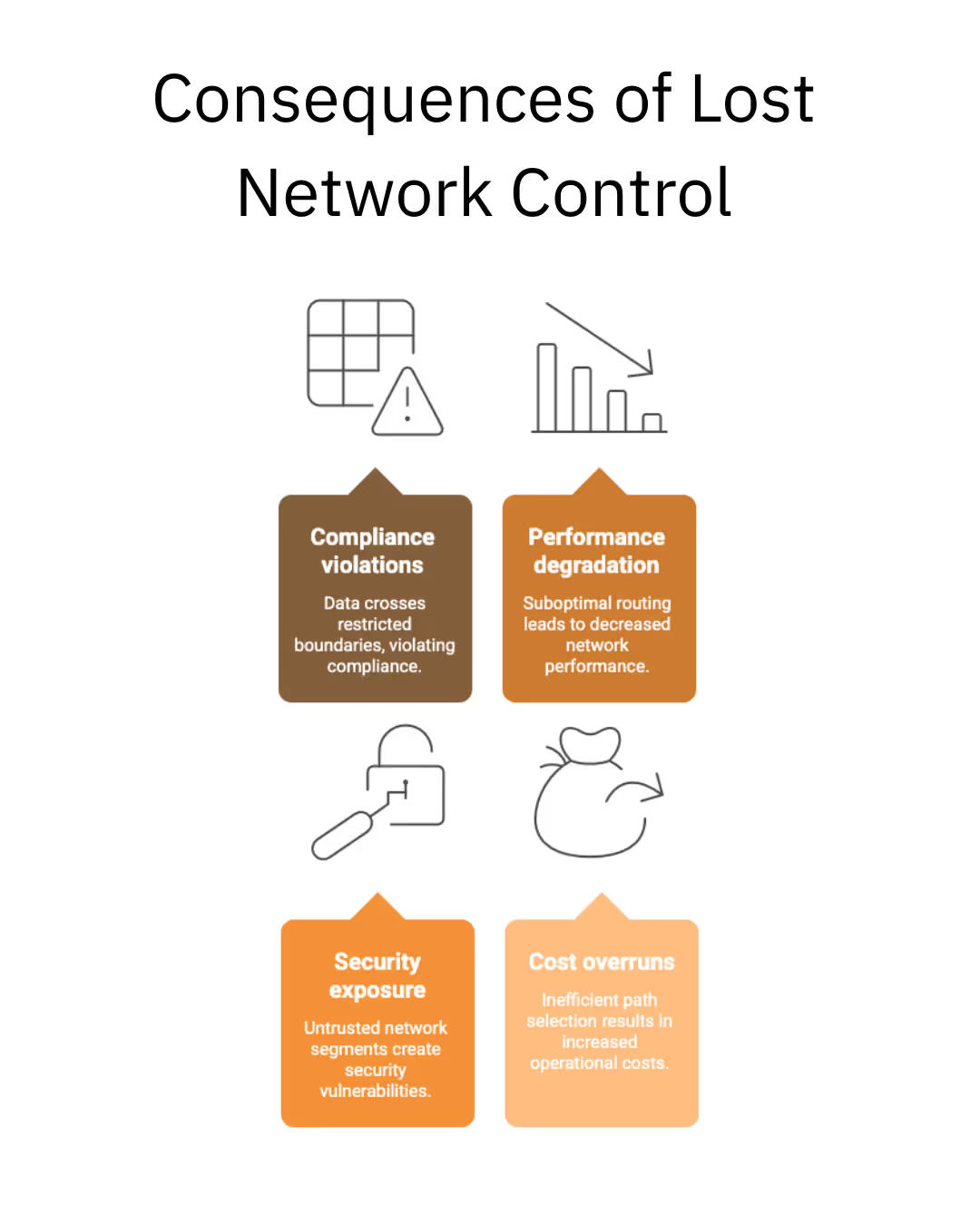
Business Continuity and Resilience: When BGP routing changes unexpectedly, due to outages, attacks, or configuration errors, it can disrupt business operations. Network sovereignty provides predictable, controlled routing that maintains business continuity regardless of external network changes.
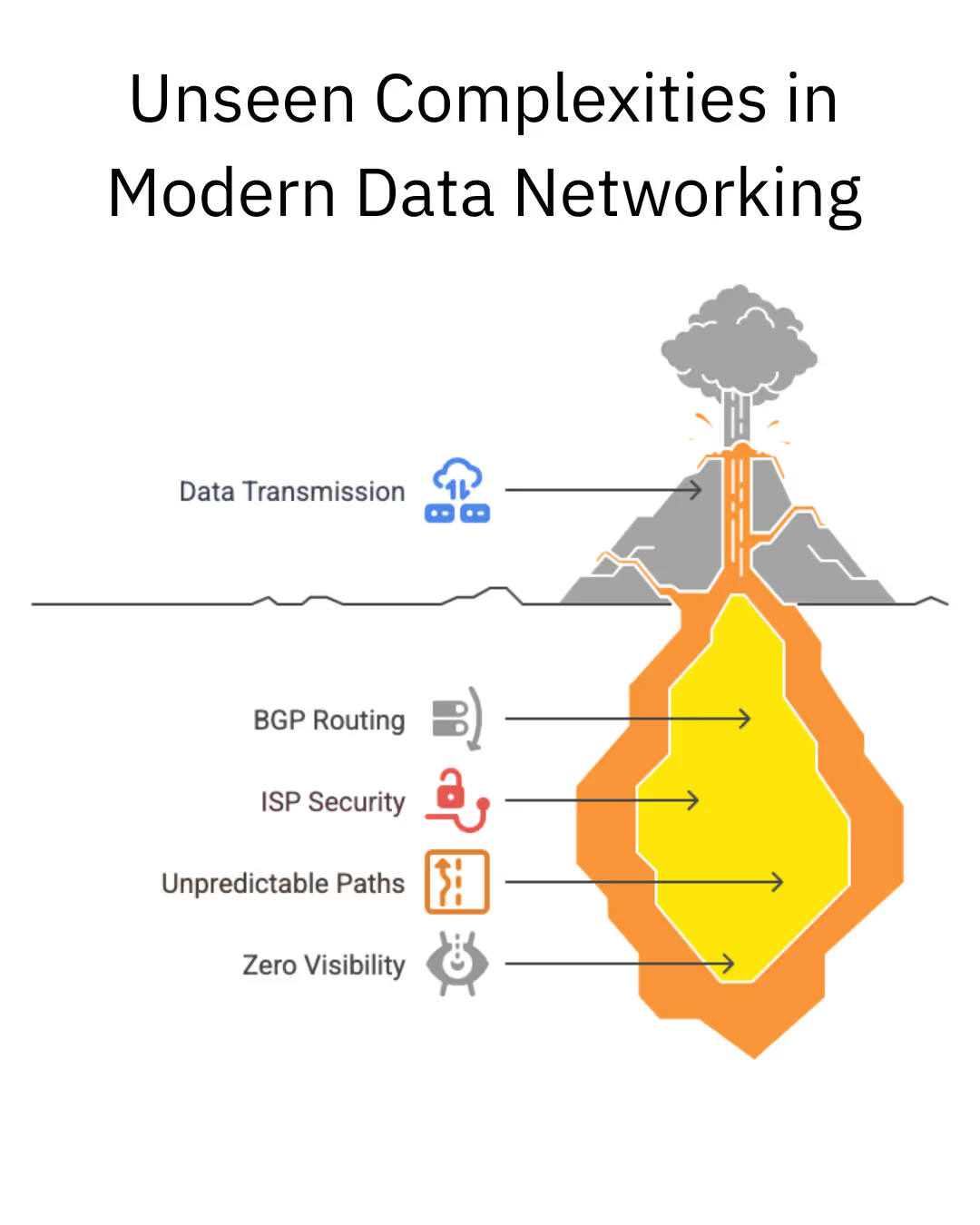
Network sovereignty means you, not BGP, decide how your data travels between destinations. Traditional networking relies on BGP (Border Gateway Protocol) to automatically select routes based on factors you can't control. With network sovereignty, you set the rules: route by latency, cost, compliance requirements, or security preferences. Your data follows paths you choose, through networks you trust.
By deploying your own noBGP routing nework - you create an overlay network that sit above traditional BGP routing. Instead of sending traffic directly through public internet routes, noBGP establishes secure tunnels through your preferred network paths, whether that's private fiber, specific ISPs, or cloud provider backbones. You define the routing policies, and our platform automatically directs traffic accordingly while maintaining full visibility into every hop.
In most cases, performance improves significantly. By routing based on your actual requirements (like latency, throughput, or bandwidth) rather than BGPs default path selection.
No. noBGP includes intelligent fail over mechanisms. You can define multiple preferred paths in order of priority, and the system automatically switches to backup routes if your primary path becomes unavailable. This actually makes your network more resilient than pure BGP routing, since you control both the primary paths and the fallback options.