As networks scale, flat Layer 2 designs become inefficient and insecure. That’s where VLANs (Virtual LANs) come in, enabling you to segment traffic logically without requiring separate physical infrastructure.
In this VLAN configuration guide, you’ll learn what VLANs are, how they work, why they’re used, and how to configure them using switches, routers, and command-line interfaces. We’ll include diagrams and practical use cases. Finally, we’ll explore how noBGP takes network segmentation beyond VLANs for cloud-native and hybrid environments.
A VLAN (Virtual Local Area Network) allows you to partition a physical network into multiple logical broadcast domains. Devices in the same VLAN can communicate as if they were on the same switch, even if they’re physically separated.
VLANs rely on IEEE 802.1Q tagging, where each Ethernet frame includes a VLAN ID.
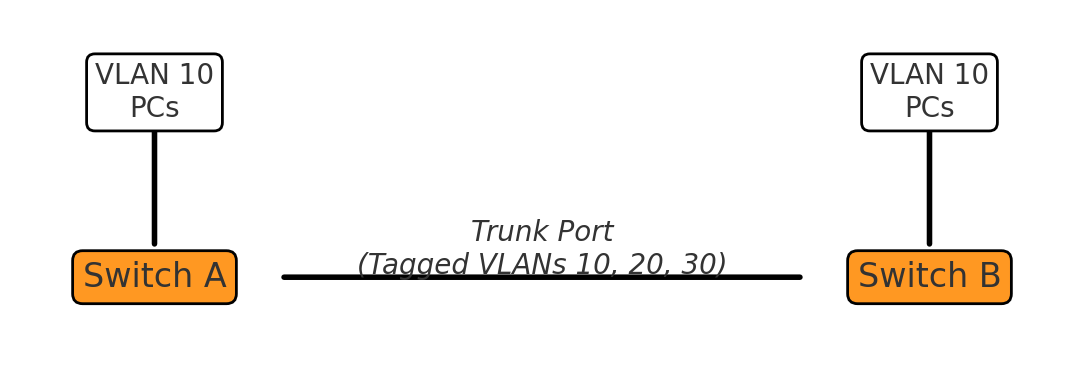
Switch(config)# vlan 10 Switch(config-vlan)# name HR Switch(config)# vlan 20 Switch(config-vlan)# name EngineeringSwitch(config)# interface fastethernet 0/1 Switch(config-if)# switchport mode access Switch(config-if)# switchport access vlan 10Switch(config)# interface gigabitethernet 0/1 Switch(config-if)# switchport trunk encapsulation dot1q Switch(config-if)# switchport mode trunk Switch(config-if)# switchport trunk allowed vlan 10,20To enable communication between VLANs, traffic must be routed—often using a router-on-a-stick setup:
Router(config)# interface gigabitethernet 0/0.10 Router(config-subif)# encapsulation dot1Q 10 Router(config-subif)# ip address 192.168.10.1 255.255.255.0Repeat for each VLAN. This creates a subinterface for each VLAN with a separate IP address.
While VLANs are essential in LAN and campus environments, they come with drawbacks:
In cloud-native environments with dynamic workloads, VLANs don’t scale well. They weren’t designed for Kubernetes pods, serverless workloads, or multi-region deployments.
VLANs are a legacy solution for segmenting Layer 2 networks. But they’re brittle, manual, and limited to local networks. noBGP replaces VLANs with policy-based, service-level segmentation that works across clouds, containers, and data centers.
VLANs are still useful, but they’re increasingly outmatched by today’s distributed, cloud-first infrastructure. You can’t trunk VLANs to AWS or segment Kubernetes pods using switch CLI.
noBGP brings segmentation into the modern era with policy-based, identity-driven networking that doesn’t rely on physical topologies or subnet math.
If you’re tired of managing VLANs, trunks, and static IPs, it’s time to choose a path that scales.