
Whether you’re configuring a cloud network, setting up a home router, or securing an enterprise firewall, you’ve likely encountered CIDR blocks. CIDR—short for Classless Inter-Domain Routing—is the notation system used to define IP address ranges in today’s internet infrastructure.
CIDR has been a foundational part of IP networking since the 1990s, allowing us to organize and manage IP addresses more efficiently than ever before. But for many, CIDR still feels abstract or confusing. Let’s break it down and answer the most common questions.
A CIDR block is a shorthand notation used to represent a range of IP addresses. The format is typically written as:
<IP address>/<prefix length>
For example: 192.168.1.0/24
Here, 192.168.1.0 is the base address, and /24 means the first 24 bits are the network portion. The remaining bits (in this case, 8) are used for host addresses within that network. That means this CIDR block represents 256 IP addresses (from 192.168.1.0 to 192.168.1.255).
CIDR works with both IPv4 and IPv6 addresses, although the notation looks more complex for the latter due to longer address sizes.
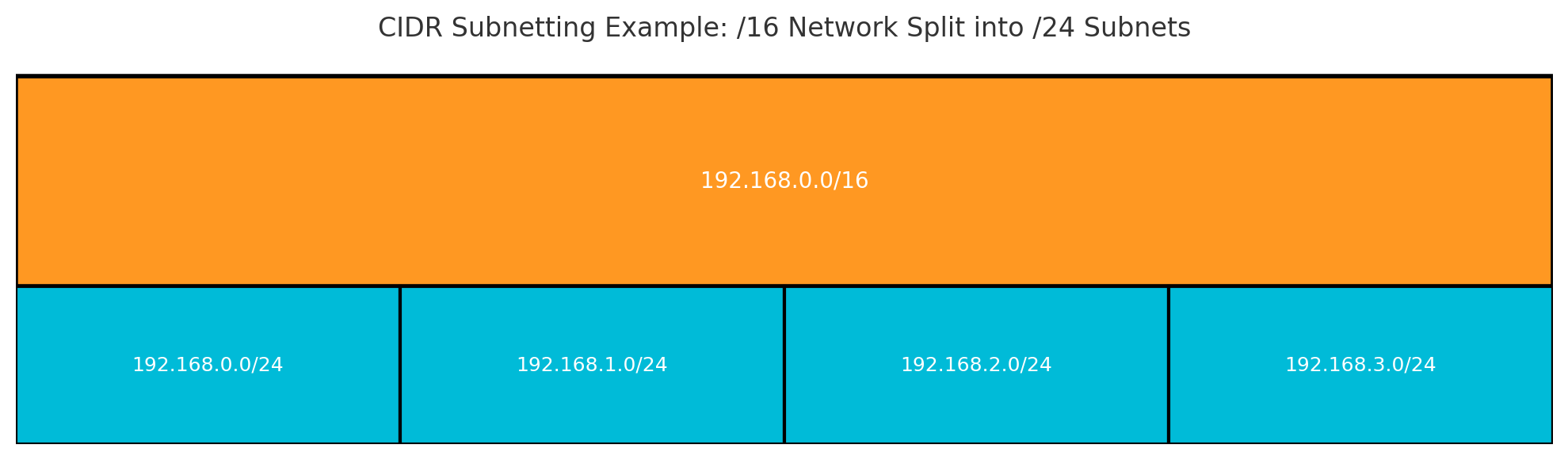
CIDR replaces the older “classful” IP addressing system (Classes A, B, C) with a more flexible approach. Instead of fixed address blocks, CIDR allows network operators to allocate addresses based on actual need.
CIDR uses variable-length subnet masking (VLSM) to divide IP address space into subnets of any size. This allows organizations to:
For example, four separate class C networks (each with 256 addresses) could be aggregated into one CIDR block like 192.168.0.0/22, simplifying routing.
This is often a misunderstood question, so let’s clarify: No CIDR range is permitted to be attacked.
However, in the context of penetration testing, ethical hacking, or network defense, professionals may scan IP ranges (defined by CIDR blocks) with explicit permission from the owner. For example, a cybersecurity consultant might be authorized to test the security of a company’s 10.0.0.0/16 block.
In all other cases, scanning or attacking IPs—regardless of CIDR range—is considered unauthorized and illegal.
CIDR was introduced in 1993 as a response to the growing problem of IP address exhaustion and routing table bloat caused by the rigid classful system. The formal specifications appeared in RFC 1518 and RFC 1519.
Its adoption marked a major shift in how the internet was managed, paving the way for scalable, efficient address allocation and routing practices that continue today.
CIDR blocks are used almost everywhere in network configurations:
To view CIDR assignments or browse public allocations, visit regional internet registry (RIR) sites like ARIN or RIPE NCC.
CIDR blocks—particularly public IP ranges—are assigned by Regional Internet Registries (RIRs) like:
These registries allocate blocks to ISPs, enterprises, or cloud providers, who then may further allocate or assign them to end-users. Ownership can be verified via WHOIS lookup tools that show which organization is responsible for a specific CIDR block.
Private IP ranges (e.g., 10.0.0.0/8, 192.168.0.0/16, 172.16.0.0/12) are not owned by anyone and are available for use within internal networks.
CIDR is used because it solves multiple critical problems:
Without CIDR, the internet as we know it would struggle under the weight of inefficient routing and IP exhaustion.
CIDR may look intimidating with its slashes and subnet math, but it’s one of the core technologies keeping modern networking efficient and scalable. Whether you’re a cloud architect, network admin, or just learning the basics, understanding how CIDR works will help you design better networks, secure your infrastructure, and troubleshoot IP conflicts more effectively.