Right now, someone is scanning your public IP addresses. They don't know your company name, your industry, or what you do, they just know you exist on the internet. And for an attacker, that's all they need.
Tired of playing security whack-a-mole? Every time you lock down one exposure, three more pop up. Every time you patch one vulnerability, attackers find another way in. Every time you think you've secured your perimeter, someone discovers a forgotten staging server on Shodan.
It's exhausting. And it's endless.
Welcome to the reality of having a public attack surface.
What Is the External Attack Surface and Why Does It Exist?
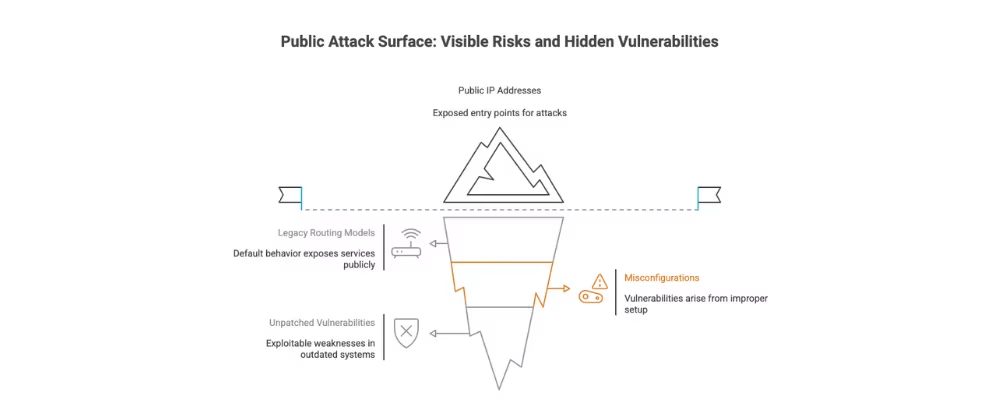
Modern networks rely on public IP addresses to establish connectivity across clouds, regions, and even data centers. This default behavior dates back to legacy internet routing models using BGP (Border Gateway Protocol). In this model, services and workloads are reachable because they are advertised publicly—intentionally or unintentionally.
But public reachability comes at a cost. Every public IP is a potential door for unauthorized access. Even if services are behind VPNs, proxies, or firewalls, they still exist on the public internet, waiting for misconfiguration or vulnerability to turn into exploitation.
Security teams respond to this risk with tools like:
- External Attack Surface Management (EASM) to identify what’s exposed
- WAFs and firewalls to control access
- SIEMs and IDS to monitor threats
But here’s the question: why expose anything at all?
noBGP Makes the Public Internet Optional
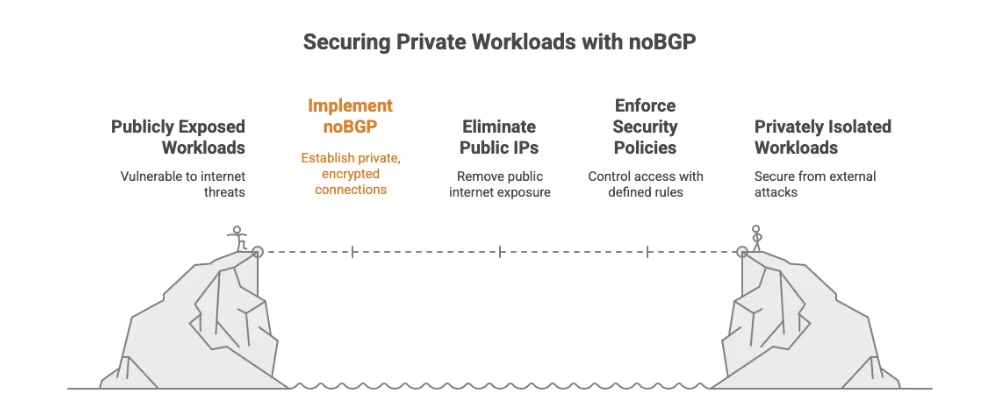
noBGP changes the game by removing the need for public IP addresses altogether. Workloads using noBGP are not advertised, not reachable, and not exposed, because they never touch the public internet.
Instead, noBGP builds private, encrypted, and deterministic connections between workloads based on policy, not location or subnet. No port forwarding. No NAT traversal. No public DNS. And crucially—no public IPs.
This approach doesn’t “secure your attack surface”, it erases it.
Security by Design, Not by Reaction
With noBGP, your security team's daily reality changes:
No more emergency patching weekends. When CVE-2024-XXXX drops for your firewall vendor, you're not scrambling, because there's no perimeter to patch.
No more 3 AM port scan alerts. Your SIEM isn't flooded with "reconnaissance activity detected" because there's nothing for attackers to reconnaissance.
No more explaining Shodan discoveries to executives. That awkward board meeting where you explain why your "internal" database showed up on a public search engine? It can't happen when your services aren't publicly routable.
No more VPN complexity tax. Your DevOps team isn't troubleshooting tunnel failures, managing certificates, or explaining why the London office can't reach the Singapore API.
No more shadow IT surprises. When developers spin up cloud resources, they can't accidentally expose them to the internet, because noBGP networks don't have a public internet connection to expose to.
Unlike traditional networks that rely on perimeter defenses and access controls layered onto inherently exposed infrastructure, noBGP creates networks that are private by default.
Everything else is just policy.
Why You Don’t Need EASM for noBGP
You shouldn't have to discover your own infrastructure on the dark web. Yet that's exactly what Imagine a world where your security team sleeps through the night. Where "zero-day" announcements don't trigger panic. Where your CEO never has to explain a breach that started with basic reconnaissance.
That world isn't a fantasy. It's what happens when you remove the attack surface entirely. Database ports accidentally opened to the world.
It's like having to hire a private investigator to tell you what's in your own house.
With noBGP, these tools become irrelevant. There is no attack surface to discover, because nothing is on the public internet to begin with.
Security isn’t something bolted on after exposure, it’s built into the noBGP architecture.
A New Approach for a New Era
The cloud, DevOps, and zero trust have changed how infrastructure is built—but most networks are still held together by 1990s-era assumptions. Public IPs. BGP. VPNs. Firewalls.
noBGP lets you step into a world where:
- Workloads communicate directly and securely without being publicly routable.
- There is no risk of lateral movement from exposed services, because they’re not exposed.
- Security teams can focus on securing what matters, not inventorying exposure.
If you're building infrastructure for security, privacy, or compliance, you no longer have to work around the public internet. You can choose a new path: one where your workloads are never exposed in the first place.
This is network sovereignty, complete control over your infrastructure's reachability and connectivity, independent of public internet routing decisions.
The Future Doesn’t Have a Public Edge
Your network shouldn’t rely on hiding or securing public entry points. It should remove them altogether.
noBGP lets you do exactly that.
If you’re building infrastructure for security, privacy, or compliance, you no longer have to work around the public internet. You can choose a new path: one where your workloads are never exposed in the first place.
And when there’s no external or public attack surface, there’s nothing to attack.
Ready to eliminate your attack surface?
FAQ:
Q: What is an external attack surface and why is it dangerous?
A: An external attack surface refers to all the publicly accessible entry points in your network infrastructure that attackers can discover and potentially exploit. This includes public IP addresses, open ports, web applications, and any services reachable from the internet. The danger lies in the fact that every public IP address acts as a potential doorway for unauthorized access. Even when protected by VPNs, firewalls, or proxies, these services remain visible on the public internet, making them vulnerable to reconnaissance, scanning, and exploitation. Attackers can use tools like Shodan to discover exposed services, and any misconfiguration or unpatched vulnerability can lead to a successful breach. The challenge is that traditional security approaches focus on securing these exposed surfaces rather than eliminating them entirely.
Q: How does External Attack Surface Management (EASM) work?
A: External Attack Surface Management (EASM) is a cybersecurity approach that helps organizations identify, monitor, and secure all their internet-facing assets. EASM tools continuously scan the public internet to discover exposed services, open ports, subdomains, and other externally accessible infrastructure that belongs to your organization. These tools work by performing reconnaissance similar to what attackers do - port scanning, DNS enumeration, and certificate monitoring. EASM solutions then provide visibility into your attack surface, alert you to new exposures, and help prioritize remediation efforts. However, EASM is fundamentally reactive - it helps you find and secure what's already exposed, rather than preventing exposure in the first place. Organizations often discover their own infrastructure through EASM tools, sometimes finding services they didn't know were publicly accessible.
Q: What is noBGP and how does it eliminate attack surfaces?
A: noBGP is a network architecture approach that eliminates external attack surfaces by removing the need for public IP addresses entirely. Unlike traditional networks that rely on BGP (Border Gateway Protocol) routing and public internet connectivity, noBGP creates private, encrypted, and policy-based connections between workloads that never touch the public internet. Instead of securing publicly accessible services, noBGP ensures that services are never publicly advertised or reachable in the first place. This means no port forwarding, no NAT traversal, no public DNS entries, and crucially, no public IP addresses. Workloads communicate directly and securely through private networks based on policy rather than location or subnet configuration. This architectural shift moves from "security by reaction" to "security by design," making traditional perimeter defenses and attack surface management tools unnecessary.
Q: Why don't I need EASM tools with noBGP networks?
A: You don't need External Attack Surface Management (EASM) tools with noBGP networks because there is no external attack surface to manage. EASM tools are designed to discover and monitor publicly accessible infrastructure on the internet - but noBGP networks don't have any publicly accessible components to discover. Since noBGP workloads never receive public IP addresses and aren't advertised through BGP routing, they simply don't exist on the public internet for EASM tools to find. This eliminates the need for continuous external scanning, attack surface monitoring, and the reactive security measures that EASM tools provide. Instead of spending resources on discovering your own exposed infrastructure (which shouldn't be necessary in the first place), noBGP lets you focus on securing what actually matters while ensuring that nothing is inadvertently exposed to external threats.

