
In June 2021, a major BGP routing error caused Fastly's content delivery network to fail, taking down Amazon, Reddit, and countless other websites. For several hours, large portions of the internet simply disappeared. This wasn't a sophisticated cyber attack - it was a configuration mistake in the Border Gateway Protocol (BGP), the internet's core routing system that most users never think about.
A key player in this process is the **Border Gateway Protocol (BGP)**, which allows independent networks to exchange information and keep the internet connected. This article breaks down the basics of BGP, explains its necessity for global connectivity, and discusses the complexities of routing that make data paths unpredictable and insecure. Understanding BGP functions shows why it impacts network performance and data security.
Imagine if every time you mailed a letter, each post office along the way had complete freedom to send it wherever they wanted, with no central authority controlling the route. That's essentially how the internet works, with Border Gateway Protocol (BGP) serving as the postal service's routing system. When you load a website or send an email, your data travels through thousands of independent networks called **Autonomous Systems (ASes)**, each making its own decisions about where to send your information next.
Each AS is managed by an organization, such as an internet service provider (ISP), a large enterprise, or a content provider like Google or Facebook. These ASes communicate and share information about available paths, which is where BGP is utilized.
Autonomous Systems (AS) are networks controlling a unique collection of IP addresses and routing policies. Each AS operates independently, determining its own internal routing rules based on its priorities—speed, cost, or security. It uses BGP to announce reachable IP ranges to connect with other networks and enable global internet access. These announcements inform other ASes of reachable IP addresses, forming a data path network for BGP to route traffic.
Diagram: A simple illustration shows Autonomous Systems (ASes) as nodes linked by BGP paths, labeled as ISP, corporate network, or content provider.
The BGP system functions like an internet map, constantly updating to reflect current routes between networks. When one AS advertises a new IP range or route, other ASes can use this information to route data efficiently. However, while BGP provides a method for data to find a path, it doesn't guarantee the fastest or most direct path. This flexibility is essential for connectivity but problematic for performance and security.
While BGP has evolved since its 1989 debut, recent incidents highlight its struggles to keep up with today's threats:
- In 2018, hackers used BGP hijacking to steal $152,000 in cryptocurrency by redirecting traffic to their servers
- In 2020, a CenturyLink BGP configuration error caused widespread outages affecting Cloudflare, Discord, and other major services
- In 2021, Facebook's BGP misconfiguration led to a six-hour global outage, costing the company an estimated $65 million
These incidents aren't just technical glitches - they represent real economic and social impacts that affect billions of users.
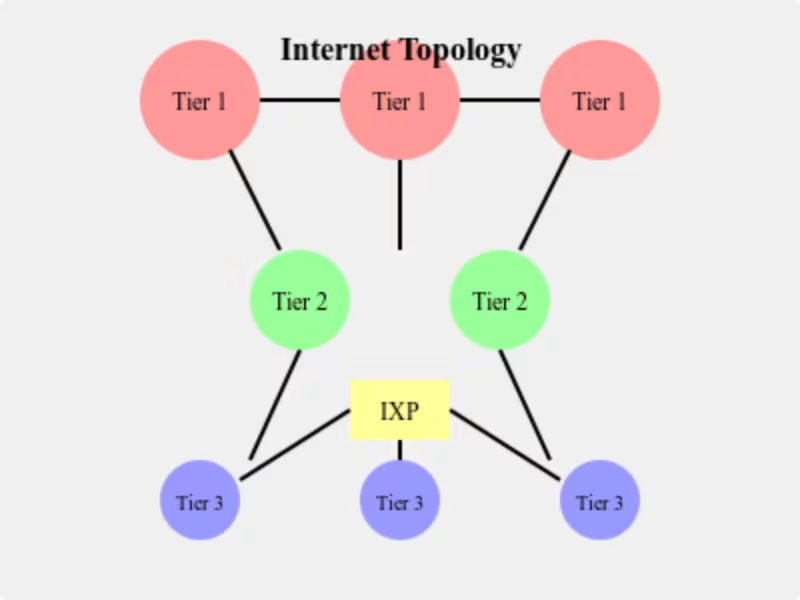
When you click a link or send a message, your data embarks on a journey through what's essentially a three-tiered highway system. Understanding this structure reveals why your internet experience can vary dramatically from moment to moment:
The Internet consists of _Tier 1_, _Tier 2_, and _Tier 3_ Internet Service Providers (ISPs), and other entities like content delivery networks (CDNs) and Internet Exchange Points (IXPs). Let’s break that down:
- Tier 1 ISPs are the Internet backbone providers. They have massive global networks and interconnect to form the top layer of the Internet. They don’t pay other providers for transit; instead, they peer directly.
- Tier 2 ISPs: These regional providers often buy transit from Tier 1 ISPs but can also peer with other Tier 2 networks or directly with Tier 1. They provide Internet services to other networks and businesses but lack the global reach of Tier 1 ISPs.
- Tier 3 ISPs are at the bottom of the hierarchy. They are local or regional ISPs that purchase Internet services from Tier 2 providers. They offer access directly to end-users like households and small businesses.
- Internet Exchange Points (IXPs) are physical locations where different networks meet to exchange traffic. They reduce reliance on upstream providers and keep local traffic within a region, improving performance and lowering costs.
Each layer relies on BGP to route traffic between autonomous systems. Tier 1 ISPs handle a significant portion of global Internet traffic, while Tier 2 and Tier 3 ISPs manage regional and local traffic. When you visit a website, your data moves across several tiers, crossing multiple autonomous systems.
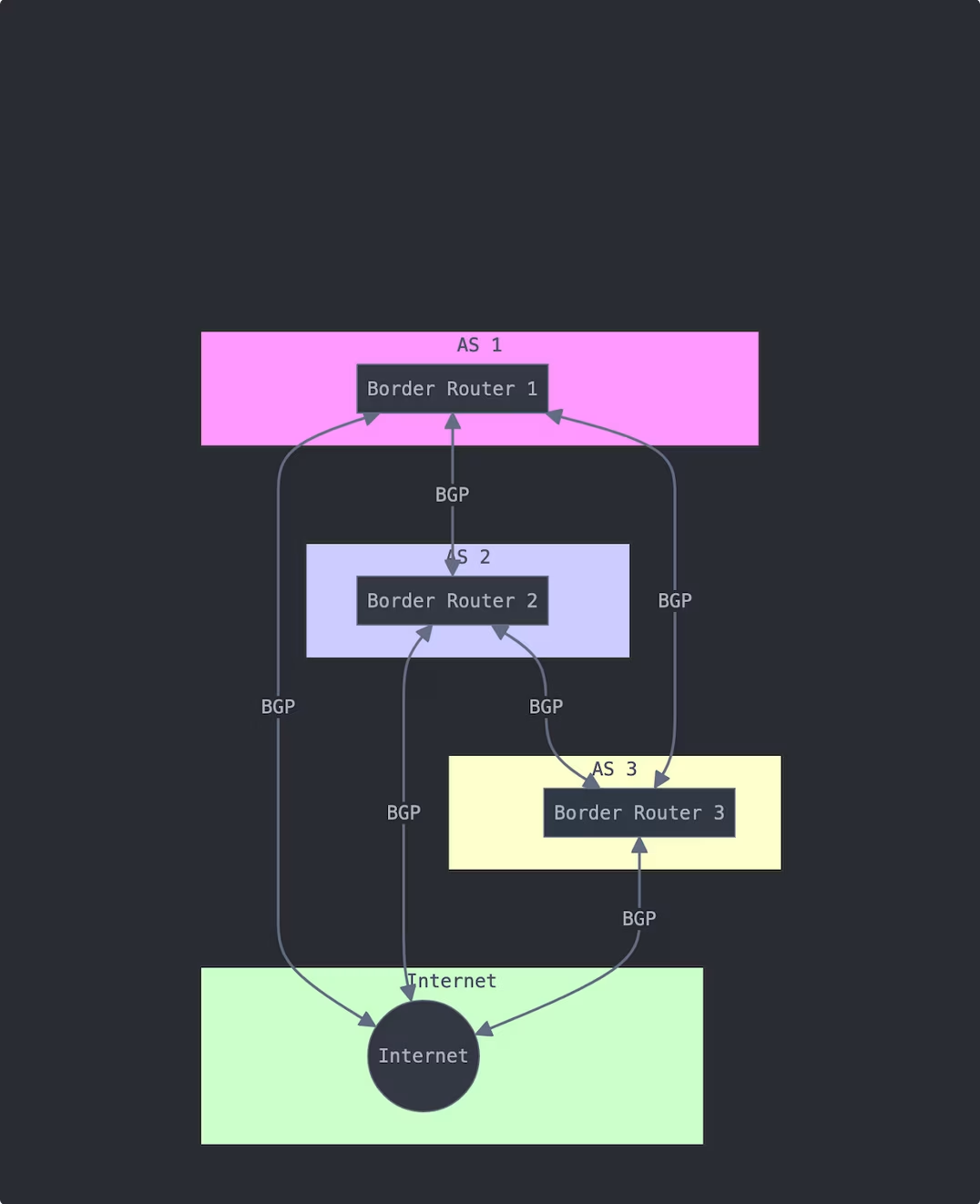
Imagine you're using a GPS app where every driver can suddenly create or remove roads at will, and each navigation company can prefer different routes based on secret deals they've made. That's essentially how BGP works. Instead of roads, we have **route announcements** - messages that networks send to each other saying "I know how to reach these destinations."
Here's a real-world example: When Netflix streams a video to your device, their servers might announce: "We can reach these IP addresses through our network." Your ISP and several other networks along the way each make their own decisions about the best path to reach Netflix, creating a complex web of possible routes.
When data travels between ASes, BGP examines available routes and selects a path based on criteria that do not necessarily prioritize the fastest or most direct route. It considers AS-path length (the number of ASes the data passes through) and routing policies defined by each AS. For instance, an AS may prioritize certain connections based on agreements with others or the cost of routing data through specific paths.
This path selection process enables BGP to route data flexibly, but it also makes routing complex and unpredictable. Each AS has its policies and preferences; routing can change dynamically, and different paths may be chosen based on changes in traffic patterns or network status.
Diagram: A simple illustration shows three different ASes with multiple potential paths between them. This emphasizes that BGP selects a route based on path length and other criteria rather than preference.
Imagine a user in California accessing a website hosted on European servers. The data to load that website could travel across multiple ASes, taking a path that balances length and policy constraints rather than direct distance. If BGP determines a slightly longer route is preferable due to AS policies or agreements, a direct path from California to Europe might not be chosen. This approach allows global flexibility, but data doesn't always take the most efficient route.
The most distinctive—and potentially concerning—feature of BGP is its non-deterministic nature. Once data leaves an AS, users or companies don't control its path. Instead, it dynamically determines the route based on shifting announcements and network conditions. This flexibility is necessary to accommodate the vast number of interconnected networks on the internet, but it introduces unpredictability.
This lack of control can be challenging for companies. An organization can manage and optimize its internal network for performance or security but loses control once data exits its AS. Once data traverses others, it's subject to their routing policies and agreements, which may not align with the company's priorities. This routing can introduce issues like increased latency, inefficient paths, and security risks if data passes through less secure or untrusted ASes.
Example Scenario: A financial institution with New York and London data centers prefers a direct, low-latency route for sensitive transactions. However, due to BGP's path selection criteria and lack of end-to-end control, the data may travel through multiple intermediate ASes, increasing latency and exposure to untrusted networks.
The non-deterministic nature of BGP routing can significantly impact data security and performance. Unpredictable data routes expose organizations to **hijacking**—an attack where malicious ASes falsely advertise IP ranges to intercept traffic. Additionally, suboptimal routing increases latency and reduces the quality of real-time applications like video conferencing or financial transactions.
BGP's route selection flexibility across autonomous systems (ASes) is both its strength and vulnerability. This adaptability is critical to keeping the internet connected, but it introduces risks to data security and performance that concern businesses and individual users.
Remember when a major BGP incident in 2018 redirected Google's traffic through Russia and China for 74 minutes? This wasn't just a technical glitch - it demonstrated one of BGP's most dangerous flaws. Here's what happened:
1. An unauthorized network in Nigeria suddenly announced "We have the best route to Google"
2. Due to BGP's trust-based nature, other networks believed this claim
3. Global traffic meant for Google was redirected through potentially hostile networks
This type of incident, called BGP hijacking, happens more often than you might think:
- In 2019, European mobile traffic was mysteriously routed through China Telecom for 2 hours
- In 2020, a Russian telecom accidentally claimed ownership of Facebook's IP addresses
- In 2022, cybercriminals used BGP hijacking to steal cryptocurrency worth millions
The scariest part? These are just the incidents we caught.. In a hijacking attack, an AS could misroute sensitive information, allowing interception or monitoring by unauthorized parties.
In 2018, BGP hijacking rerouted cryptocurrency transactions by exploiting BGP's route announcements, redirecting traffic through an unauthorized AS to steal funds. This incident highlights BGP's risks for industries dealing with sensitive transactions, such as finance, healthcare, and government. Organizations cannot guarantee secure data routes, which is problematic for sensitive data.
Besides security, BGP's route selection can impact performance by choosing paths that aren't optimized for speed or efficiency. Since it doesn't prioritize the shortest or fastest route, data can be sent through indirect or congested paths, leading to higher latency and inconsistent performance. This can affect time-sensitive applications like video conferencing, online gaming, or financial trading, where slight delays can be disruptive or expensive.
A company hosting a real-time application for customers across different regions may experience performance issues if BGP routes data through several intermediate ASes instead of a direct path. This detour can lead to slowdowns, dropped packets, and other performance issues, affecting user experience and business outcomes.
In today's interconnected world, companies delivering reliable, low-latency services where user experience is crucial face challenges from BGP routing limitations.
Why does the internet still rely on BGP as its primary routing protocol, despite its drawbacks? The answer lies in its role in connecting thousands of independent networks and enabling global internet access. Despite its vulnerabilities, BGP's ability to adapt to changes in network topology is essential to the internet's resilience.
The internet consists of thousands of autonomous systems with their routing policies. BGP allows these ASes to share information and find data paths between networks. By enabling ASes to interact, BGP allows global users to access services and information regardless of their location. Without BGP's flexibility, the internet would struggle with current data traffic.
BGP's strength lies in rerouting traffic around network issues, like outages or congestion. It ensures data reaches its destination even if the original route is unavailable. This adaptability makes BGP highly resilient, capable of handling disruptions by finding alternative paths in real time.
Industry experts and organizations are working to make BGP more secure and reliable, recognizing its limitations. They have introduced protocols like Resource Public Key Infrastructure (RPKI) and BGPsec to enhance BGP security by adding validation layers for route origin and path verification. These improvements help prevent unauthorized ASes from hijacking routes, though widespread adoption remains difficult due to significant hardware upgrades and costs.
Researchers are exploring emerging technologies like software-defined networking (SDN) and AI-driven routing solutions to complement or replace traditional BGP routing with more reliable and secure alternatives.
Despite BGP's role in internet connectivity, its limitations are driving conversations within the networking community about future routing protocols. Emerging technologies like RPKI (Resource Public Key Infrastructure) and BGPsec are helping to mitigate BGP's security vulnerabilities by adding validation layers. However, these solutions address only parts of the problem and require widespread adoption. Many ASes are hesitant to adopt these protocols due to additional costs, infrastructure changes, and operational complexities.
Some industry experts believe a fundamental change in routing protocols is necessary. Alternatives under consideration include:
- Software-Defined Networking (SDN) could introduce more deterministic and controlled routing by centralizing route management and allowing real-time monitoring of data paths.
- AI and Machine Learning for Predictive Routing: Using AI to predict optimal routes provides stable, low-latency paths by analyzing traffic patterns and avoiding disruptions.
- Encrypted and Authenticated Routing Protocols: Future protocols will prioritize end-to-end encryption and stronger authentication mechanisms to enhance privacy and data security beyond BGP.
These emerging technologies are still in development, and a full transition away from BGP would be a massive undertaking due to its deep integration into global internet infrastructure. The evolving threat landscape and the demand for secure, reliable routing have pressured organizations, governments, and tech leaders to explore alternatives.
- Your company's traffic might be taking unnecessary detours through untrusted networks
- Consider implementing BGP monitoring tools to detect routing anomalies
- Evaluate multi-homing (connecting through multiple ISPs) for critical services
- Stay updated on RPKI implementation best practices
- Monitor BGP announcements affecting your network using tools like BGPmon
- Develop incident response plans for BGP-related outages
- Use VPNs for sensitive transactions to add an extra layer of security
- Keep offline backups of critical data
- Have backup communication methods ready for when BGP issues cause outages
- Push for mandatory implementation of RPKI
- Support international cooperation on BGP security standards
- Develop frameworks for accountability in routing incidents
BGP is like democracy - it's the worst system except for all the others we've tried. While it keeps the internet running, its fundamental design reflects a different era of the internet, when trust between network operators was assumed and security threats were less sophisticated.
As we've seen through numerous incidents - from cryptocurrency theft to nationwide outages - BGP's vulnerabilities affect everyone from casual users to major corporations. Yet despite these risks, the internet continues to function because network operators have learned to work within BGP's limitations while pushing for gradual improvements.
The future of internet routing likely lies in a hybrid approach: strengthening BGP through technologies like RPKI while developing next-generation protocols that better suit our modern security needs. Until then, understanding BGP's quirks and limitations remains essential for anyone who depends on the internet - which, in today's world, means practically everyone.
The search for a next-generation routing protocol is ongoing, while RPKI and BGPsec represent progress. As organizations and governments invest in securing internet infrastructure, the future may hold a new protocol that meets modern connectivity needs and offers the control and security BGP lacks.
BGP remains essential to the internet's operation. Network professionals and organizational leaders can appreciate the unseen work that keeps us connected and stay alert in the evolving landscape by understanding its complexities and limitations.
Border Gateway Protocol (BGP) is essential to global internet connectivity, routing data between independent networks. However, it has vulnerabilities that impact data security, control, and performance. This article explores BGP's strengths and limitations, highlighting why experts are considering alternatives for a more secure and reliable future in internet routing.
"Fastly outage: How one customer broke Amazon, Reddit and the wider internet" - The Guardian, June 9, 2021
"China Telecom's BGP hijacking incident analysis" - Oracle Internet Intelligence, June 7, 2019
"Facebook, Google traffic redirected to Russia in latest BGP mishap" - Ars Technica, March 2020
"BGP hijacking incident steals $2M in cryptocurrency from Canadian mining pool" - The Record by Recorded Future, February 2022
"Google goes down after major BGP mishap routes traffic through China" - ArsTechnica, November 13, 2018
"Facebook Outage: A Look at What Happened" - Cloudflare Blog, October 4, 2021
"CenturyLink / Level 3 Outage Analysis" - ThousandEyes Blog, August 30, 2020
"The Cost of Cloud Outages: Understanding the Economic Impact" - IDC Research Report, 2021 internet routing.